sebelum saya menginjakkan kaki dari dunia perwarnetan dan saya serius kuliah saya pengen tulis ini dulu :D, menurut saya ini adalah setting...
Home » Archive for Februari 2012
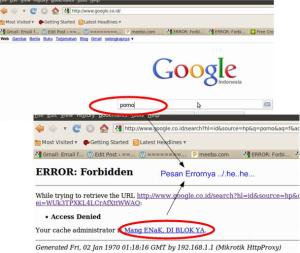 Bentar ya gue mau ketawa dulu,,wkkk.wkkkwkk…Ketawa karena bisa juga. Jadi suatu saat bos gue curhat “Bisa ga kl di Mikrotik kl kita ketikin...
Bentar ya gue mau ketawa dulu,,wkkk.wkkkwkk…Ketawa karena bisa juga. Jadi suatu saat bos gue curhat “Bisa ga kl di Mikrotik kl kita ketikin...
Posted by Unknown at 01.30,
Add Comment
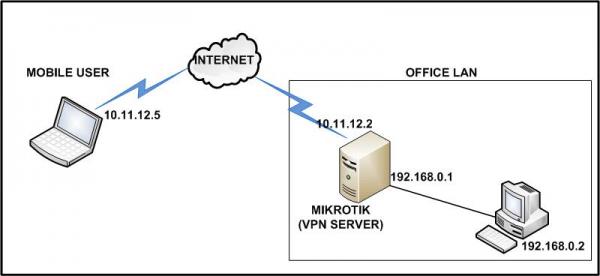 Pada tulisan sebelumnya saya menjanjikan untuk membahas mengenai implementasi VPN dengan menggunakan Mikrotik dan ClarckConnect. Pada kese...
Pada tulisan sebelumnya saya menjanjikan untuk membahas mengenai implementasi VPN dengan menggunakan Mikrotik dan ClarckConnect. Pada kese...
Posted by Unknown at 01.24,
1 Comment
 Kali ini saya sempatkan menulis catatan kecil yang mungkin sudah banyak ditulis orang lain. Selain nambah posting, lumayan bisa bikin otak...
Kali ini saya sempatkan menulis catatan kecil yang mungkin sudah banyak ditulis orang lain. Selain nambah posting, lumayan bisa bikin otak...
Posted by Unknown at 05.16,
Add Comment
 Load Balancing 2 Speedy Mikrotik RouterOS V.3.x.xx dan V.4.x.xx Langka pertama Ip modem 1 192.168.1.1 Ip modem 2 192.168.2.1 colokkan...
Load Balancing 2 Speedy Mikrotik RouterOS V.3.x.xx dan V.4.x.xx Langka pertama Ip modem 1 192.168.1.1 Ip modem 2 192.168.2.1 colokkan...
Posted by Unknown at 05.01,
Add Comment
 / ip address add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local comment=”” \ disabled=no add addres...
/ ip address add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local comment=”” \ disabled=no add addres...
Posted by Unknown at 04.59,
Add Comment
 Setup hotspot anda Buat sebuah server Radius / radius add service=hotspot address=127.0.0.1 secret=09876 Set profile pada langkah 1 unt...
Setup hotspot anda Buat sebuah server Radius / radius add service=hotspot address=127.0.0.1 secret=09876 Set profile pada langkah 1 unt...
Posted by Unknown at 04.50,
Add Comment
 Tutorial berikut berisi tentang instalasi squid. untuk isi dari squid.conf nya diambil dari tulisan balinux.or.id, yang dibuat oleh saudara...
Tutorial berikut berisi tentang instalasi squid. untuk isi dari squid.conf nya diambil dari tulisan balinux.or.id, yang dibuat oleh saudara...
Posted by Unknown at 04.45,
Add Comment
 Install CentOS 5.5 untuk mode server adalah Seperti Gambar di bawah ini : 1. Mode Linux Text agar install nya lebih cepat. Ketik Linux Text...
Install CentOS 5.5 untuk mode server adalah Seperti Gambar di bawah ini : 1. Mode Linux Text agar install nya lebih cepat. Ketik Linux Text...
Posted by Unknown at 04.40,
Add Comment
Posted by Unknown at 04.36,
Add Comment
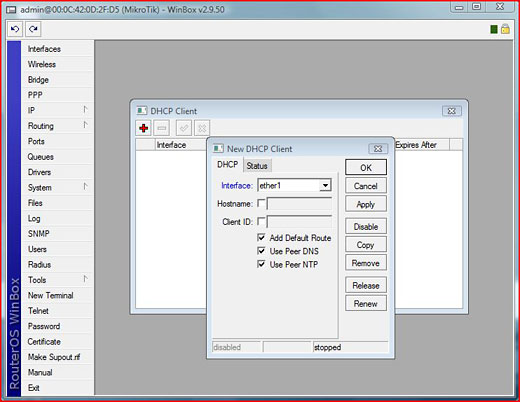 You need to setup your Mikrotik router by using Winbox. Winbox is the graphical user interface for configuring the Mikrotik Router OS. You ...
You need to setup your Mikrotik router by using Winbox. Winbox is the graphical user interface for configuring the Mikrotik Router OS. You ...
Posted by Unknown at 17.57,
Add Comment
Langganan:
Postingan (Atom)